A ‘whitehat’ hacker scored some serious cash for identifying security vulnerabilities in Oculus VR’s developer portal. The exploits, which could have been used to plant malicious code in the Oculus SDK, among other mischievous things, have been patched and the hacker rewarded through Facebook’s ‘Bug Bounty’ program.
A ‘whitehat’ hacker scored some serious cash for identifying security vulnerabilities in Oculus VR’s developer portal. The exploits, which could have been used to plant malicious code in the Oculus SDK, among other mischievous things, have been patched and the hacker rewarded through Facebook’s ‘Bug Bounty’ program.
Whitehat hackers are those that probe for security vulnerabilities with the hope of finding them before malicious hackers do. Some companies hire their own whitehat hackers and others have whitehat reward programs to encourage hackers to find and report exploits.
 With Facebook’s acquisition of Oculus VR becoming official in July, the VR company is now covered under the social network’s Bug Bounty program which also covers other companies acquired by Facebook: Instagram, Parse, Onavo, and Moves.
With Facebook’s acquisition of Oculus VR becoming official in July, the VR company is now covered under the social network’s Bug Bounty program which also covers other companies acquired by Facebook: Instagram, Parse, Onavo, and Moves.
A whitehat hacker, who goes by Jon (aka Bitquark), decided to take a look under the hood of the Oculus Developer Center, the official portal which hosts developer downloads and forums for discussion. What he found was several dangerous vulnerabilities that Facebook deemed worthy of a $25,000 reward. He blogged about the find here.
Jon, who has squashed bugs for Google, Tesla, and others who run similar reward programs, explains a bit about how he was able to achieve ‘shell’ access on the Oculus Developer Center server, after gaining access to admin privileges, enabling deep control over the server.
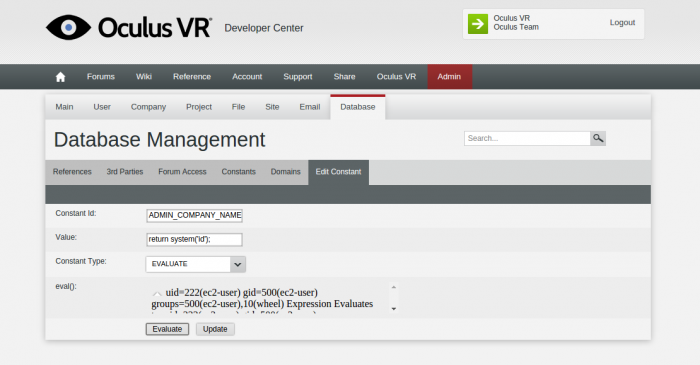
The Oculus admin user has access to a special admin panel containing all sorts of goodies. I could edit users and projects, add news articles, edit the dashboard, upload SDK files, all sorts. I was about to try uploading a PHP shell when something else caught my eye.
In PHP, the eval() function is a dangerous thing. It allows you to directly execute a string as PHP code, which in turn lets you do fun things like execute system() commands, so I was surprised to find it used freely in the admin portal. I’ll let the screenshot speak for itself, but suffice it to say I now had a shell on the Oculus development centre server.
After achieving this level of access, Jon says a malicious attacker could have done any manner of dangerous things from accessing the personal information of several hundred thousand developers who are registered in the Developer Center, to planting malicious code on the server and even in the Oculus SDK and perhaps the Oculus Runtime.
Fortunately for the VR community, Jon reported his findings to Facebook. The company, which awards a minimum of $500 per bug, opted to give Jon $25,000 in total for the vulnerabilities he identified.
“All in all, it’s been a pretty productive week :-),” Jon wrote.